

- Cisco Remote Access Client
- Cisco Remote Access Vpn
- Cisco Remote Access Vpn License
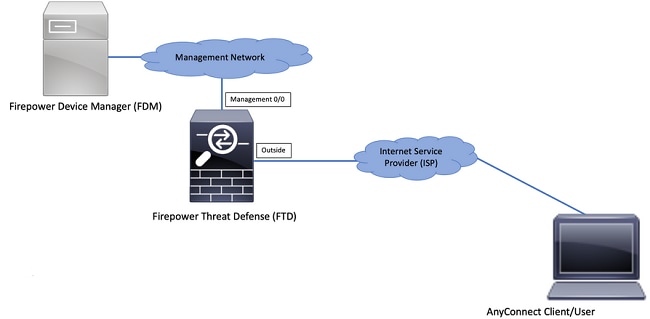
In my previous post I gave you some recommendations on why use a VPN. Today I want to explain you how to configure remote access it using a Cisco Firepower Threat Defense (FTD) firewall managed by Firepower Management Center (FMC).
Latest apple software. How to configure Remote Access VPN step by step:
Now we will see how to configure a FTD device, to allow AnyConnect connections and to use an internal Microsoft NPS server for authenticating the users.
- Windows 10 client
- Cisco virtual FTD running version 6.6.0
- Cisco FMC running version 6.6.0
Problem in Cisco Remote access VPN. Hi Experts, Kindly help in solving the problem in remote access vpn. I configured Remote access VPN on cosco asa 5510 evrything is working fine i can able to connect internet. On that machine but user cannot able to connect using easy vpn client 5.0 to its server. To determine the best tool for your needs, first visit Remote Access to the UD Network. Connecting a VPN session; Using a VPN session to access your office computer from home; Disconnecting a VPN session; DOWNLOAD FOR WINDOWS NOW Connecting A VPN Session. Open your newly installed Cisco. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router. The configurations in this chapter utilize a Cisco 7200 series router.
FMC configurations:
Create a new certificate for FTD
On FMC go to “Devices –> Certificates” and click on “Add Certificate”.
On the tab that will be showed please select the FTD where you want to add the certificate and who is enrolling that certificate.
In our guide we are using FMC as internal CA, that it’s a self signed certificate. We are not using a corporate CA or an external CA.
When the certificate is created we can go over and add our radius server on FMC.
Add radius server on FMC
On FMC go to “Object –> Object Management –> Radius Server Group –> Add Radius Server”
I created an object called SRV-NPS-GRP that contains all my Radius servers. For adding the radius server you can just click on “+” and specify your NPS server.
Keep in mind that the key used for adding the new radius server must be used on NPS Radius client. It’s a pre-shared key.
Add pool of addresses for VPN client
On FMC go to “Object –> Object Management –> Address Pools –> Add IPv4 Pools”
You need to specify the subnet that will be used from a VPN client. In the field “IPv4 Address Range” it’s not necessary to specify a subnet but just a range of IP Address. At the end click the save button.

Uploading AnyConnect Images
On FMC go to “Object –> Object Management –> VPN –> AnyConnect File –> Add AnyConnect File”
You need to upload .PKG file that you must download from cisco.com. A client that tries to connect on our firewall with an obsolete AnyConnect version or without it will download our version of software.
Configure Remote Access VPN
On FMC go to “Devices –> VPN –> Remote Access –> Add a new configuration”
Assign the new VPN policy to the firewall and then click “Next”
On the next configuration menu you must select your Radius group that you have configured before and the IPv4 Address Pools, like the image below. After that you can click “Next”
Cisco Remote Access Client
On the next menu you need to choose the AnyConnect package that you want to use. If you want to enable AnyConnect for MAC please ensure that you have a valid package.
Cisco Remote Access Vpn
On the next menu you need to select the interface where you have to enable the SSL VPN access and which certificate you need to use for establishing VPN tunnel.
If you enable “Bypass Access Control policy for decrypted traffic” you are not able to perform any kind of filter on Access Policy from incoming VPN traffic.
At the end of wizard you are able to see your remote access VPN profile on your FMC.
Configure no NAT policy
The last step needed on FMC is to configure a new NAT policy to avoid that the traffic from the LAN to the VPN client will be natted.
Now you are able to deploy the configuration to you FTD!
We need to perform last steps on Windows NPS before to say that we have finished to configure a remote access VPN on Cisco FTD
Windows NPS configuration
On the Windows server you must enable the role of Network Policy Server, after that you can configure NPS service.
In my scenario I’m limiting the VPN access only to the user who is a member of a specific Windows Security Group called SG_VPN. In this way you can authorize who can connect via VPN or not.
You need to add a new Radius client on your NPS server, so right-click on “Radius Clients” and select “New”.
In settings you need to specify the FTD firewallIP address and pre-shared key used previously on FMC.
As last step you need to create a new Network Policies for authenticating the VPN user. As you can see in the image below I’m applying a filter on Windows Groups. In this way I can control who can access to my VPN.
We are at the end, so you can launch your AnyConnect client and try to connect to your firewall.
Cisco Remote Access Vpn License
I hope that this post about how to configure remote access VPN on Cisco FTD was cool and stay tuned on ITornAgeek for new posts!!!




