- Sshdconfig is the OpenSSH server configuration file. How to configure and troubleshoot. Avoid getting accidentally locked out of remote server.
- The sshdconfig file is an ASCII text based file where the different configuration options of the SSH server are indicated and configured with keyword/argument pairs. Arguments that contain spaces are to be enclosed in double quotes ('). In the sshdconfig file the keywords are case-insensitive while arguments are case-sensitive.
High Speed Premium VPN and Fast SSH ServerSSH dropbear - High Speed Premium VPN and Fast SSH Server, High Data Transfer High Speed Connection SSH account, ssh account 30 days, ssh server, free ssh. Setting up SSH Server on your Kali Linux machine, And connect through SSH Client From your Mac OS X or Windows. Visit: http://goo.gl/CSKnwD.
If you are even a tad bit familiar with SSH, you know that you can use it to connect to remote Linux systems.
Using SSH to connect to remote system is simple. All you need to do is to use a command like this:
This connects to the default SSH port 22. You may specify the port as well if you want.
Now this is all plain and simple if you just have one server. Even if you don’t remember the server’s IP address, you can perform a reverse search to the history using the famous terminal keyboard shortcut Ctrl+R and find the SSH command you used in the past.
But things get complicated when you have several servers to manage. I have around ten servers that I connect to from time to time. Some are production servers and some are test servers.
Now keeping a track of these servers is not easy. Even if I can find the SSH commands from the history, it is difficult to guess which IP belongs to which server.
Of course, I can open my dashboards on Linode, UpCloud, DigitalOcean and Google Cloud to get the IP or keep a list on my local system.
A better and easier way is to use SSH config file.

Using SSH config file for easily connecting to remote servers
The SSH config file allows you to create different profiles for different host configurations. There is no limit to such profiles and you may add as many as possible.
So, if you connect to multiple remote systems via SSH, creating SSH profiles will be a good move to save your time.
Let me show you how to use it.

Step 1: Create the SSH config file
When you install SSH, you’ll have a ~/.ssh directory created automatically. This direct contains your public key, private key a known_hosts file. Your config is also stored here.
At least on Ubuntu, the SSH config file is not created by default. You can easily create this file using the touch command like this:
Step 2: Add an SSH profile in the config file
Now that you have the SSH config file, you can edit it using Vim or Nano. Let me show you an example of the syntax which you should follow.
Let’s say you connect to a server with IP 275.128.172.46. Your username is Alice and the server is used for hosting your website. To harden SSH security, you use port 1500 instead of the default SSH port 22.
You can add all this information in the following manner in your ~/.ssh/config file:
Just save the information in the file. No need to restart any service.
Now, instead of writing a long command like this:
You can just use this command (tab completion works as well):
When you run the above command, ssh looks for a Host named website in the ~/.ssh/config. If it finds a host with that name, it gets all the information related and used it for making an SSH connection.
You might wonder about a few things, so I’ll mention it here:
- There is no space or tab indention restriction while entering the host information. Space or tab indention are used for making the config file easily understandable.
- The Hostname can be the IP address of the server or a hostname that can be resolved on your network.
- All the parameters like hostname, user and port are optional. However, I personally advise keeping at least hostname because that’s what you need (and you forget) most of the time.
- If your SSH config file is wrongly configured, it will result in an error when you try to use it for SSH connection.
- You cannot save passwords in SSH config. I advise adding your public SSH key to the server for easy access.
Step 3: Adding multiple profiles in SSH config file
The previous step gave you an idea about how to add an SSH profile. Let’s take it to the next step by adding multiple profiles in it.
Here’s what the SSH config file looks like now:
This time, I have added four different SSH profiles in it.
Did you notice the Host * entry at the end of the file? You can use this entry to for adding a parameter common to all profiles if that parameter hasn’t been mentioned for the profile explicitly.
So if I try to use the main-server SSH profile, it will automatically take root user.
ssh main-server = ssh root@275.128.172.49
Order of the SSH configuration
The ssh configuration follows the following order:
- command-line options
- user’s configuration file (~/.ssh/config)
- system-wide configuration file (/etc/ssh/ssh_config)
This means that the priority is given to the command you enter and then it looks into ~/.ssh/config and then in /etc/ssh/ssh_config.
So, if you want to override a profile, you can do that using the -o option of the ssh command.
For example, if I use this command:
It will take user bob instead of the user alice as defined in the ~/.ssh/config (in the previous step).
There’s a lot more to SSH config
To be honest, there is so much more to SSH config file that cannot be covered in a single article. You can use name/IP matching, subnets and what not.
The scope of this article was to introduce you to SSH config and help you create SSH profiles for easily connecting to various remote Linux systems.
You can always refer to the man page of ssh_config to know more about the parameters you can use while creating your SSH config file.
I hope this SSH tip was helpful to you. If you already use SSH config file and have a some nifty tip with you, do share it with the rest of us in the comment section.
Become a Member for FREE
Join the conversation.
Ssh Config Server Debian
Recently, Microsoft has released a port of OpenSSH for Windows. You can use the package to set up an SFTP/SSH server on Windows.
- Installing SFTP/SSH Server
- Connecting to the server

Advertisement
- In Settings app, go to Apps > Apps & features > Manage optional features.
- Locate “OpenSSH server” feature, expand it, and select Install.
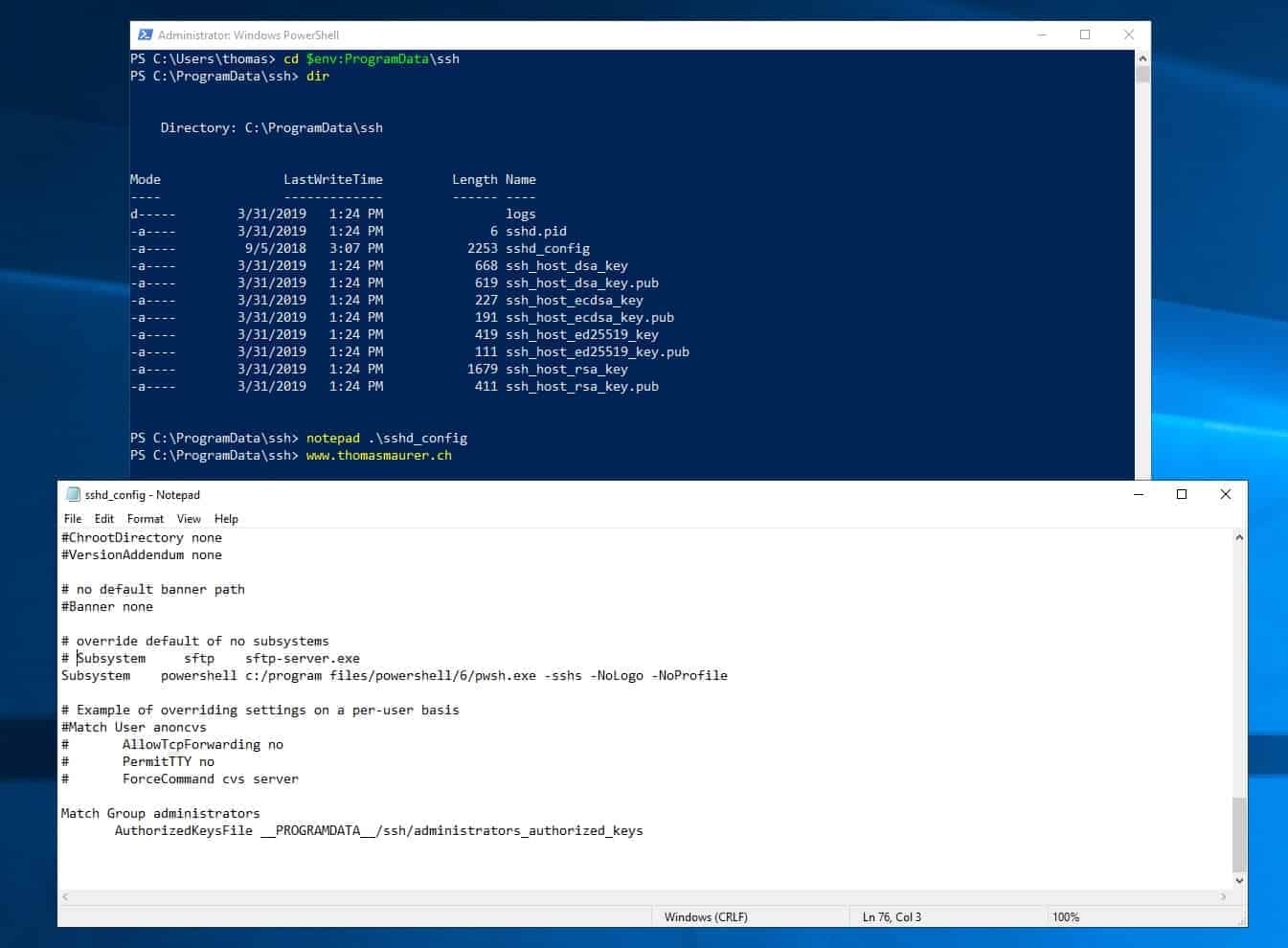
Binaries are installed to %WINDIR%System32OpenSSH. Configuration file (sshd_config) and host keys are installed to %ProgramData%ssh (only after the server is started for the first time).
You may still want to use the following manual installation if you want to install a newer version of OpenSSH than the one built into Windows 10.
- Download the latest OpenSSH for Windows binaries (package
OpenSSH-Win64.ziporOpenSSH-Win32.zip) - As the Administrator, extract the package to
C:Program FilesOpenSSH - As the Administrator, install sshd and ssh-agent services:
- Allow incoming connections to SSH server in Windows Firewall:
- When installed as an optional feature, the firewall rule “OpenSSH SSH Server (sshd)” should have been created automatically. If not, proceed to create and enable the rule as follows.
- Either run the following PowerShell command as the Administrator:
ReplaceC:System32OpenSSHsshd.exewith the actual path to thesshd.exe(C:Program FilesOpenSSHssh.exe, had you followed the manual installation instructions above). - or go to Control Panel > System and Security > Windows Defender Firewall1 > Advanced Settings > Inbound Rules and add a new rule for port 22.
- Start the service and/or configure automatic start:
- Go to Control Panel > System and Security > Administrative Tools and open Services. Locate OpenSSH SSH Server service.
- If you want the server to start automatically when your machine is started: Go to Action > Properties. In the Properties dialog, change Startup type to Automatic and confirm.
- Start the OpenSSH SSH Server service by clicking the Start the service.
These instructions are partially based on the official deployment instructions.
Follow a generic guide for Setting up SSH public key authentication in *nix OpenSSH server, with the following difference:
- Create the
.sshfolder (for theauthorized_keysfile) in your Windows account profile folder (typically inC:Usersusername.ssh).2 - For permissions to the
.sshfolder and theauthorized_keysfile, what matters are Windows ACL permissions, not simple *nix permissions. Set the ACL so that the respective Windows account is the owner of the folder and the file and is the only account that has a write access to them. The account that runs OpenSSH SSH Server service (typicallySYSTEMorsshd) needs to have read access to the file. - Though, with the default Win32-OpenSSH configuration there is an exception set in
sshd_configfor accounts inAdministratorsgroup. For these, the server uses a different location for the authorized keys file:%ALLUSERSPROFILE%sshadministrators_authorized_keys(i.e. typicallyC:ProgramDatasshadministrators_authorized_keys).
Before the first connection, find out the fingerprint of the server’s host key by using ssh-keygen.exe for each file.
In Windows command-prompt, use:
Replace %WINDIR%System32 with %ProgramFiles%, if appropriate.
In PowerShell, use:
Replace $env:WINDIRSystem32 with $env:ProgramFiles, if appropriate.
You will get an output like this:
Start WinSCP. Login dialog will appear. On the dialog:
Sshd_config Serverkeybits
- Make sure New site node is selected.
- On New site node, make sure the SFTP protocol is selected.
- Enter your machine/server IP address (or a hostname) into the Host name box.
- Enter your Windows account name to the User name box. It might have to be entered in the format
user@domainif running on a domain. - For a public key authentication:
- Press the Advanced button to open Advanced site settings dialog and go to SSH > Authentication page.
- In Private key file box select your private key file.
- Submit Advanced site settings dialog with the OK button.
- For a password authentication:
- Enter your Windows account password to the Password box.
- If your Windows account does not have a password, you cannot authenticate with the password authentication (i.e. with an empty password), you need to use the public key authentication.
- Save your site settings using the Save button.
- Login using Login button.
- Verify the host key by comparing fingerprints with those collected before (see above).
Advertisement
If you cannot authenticate to the server and use Windows 10 Developer mode, make sure that your OpenSSH server does not conflict with an internal SSH server used by the Developer mode. You may need to turn off the SSH Server Broker and SSH Server Proxy Windows services. Or run your OpenSSH server on a different port than 22.
Free Ssh Server
- Guide to Installing Secure FTP Server on Windows using IIS;
- Guide to uploading files to SFTP server;
- Guide to automating operations (including upload).
Ssh Config Serveraliveinterval
- Windows Firewall on older versions of Windows.Back
- Windows File Explorer does not allow you to create a folder starting with a dot directly. As a workaround, use
.ssh., the trailing dot will allow you to bypass the restriction, but will not be included in the name.Back
